xm commands
List Domains (Xen Guests)
# xm list
Start a Guest
# xm create [guest-config]
Connect to a guest console ( Back: ESC-] (US-keyboard), Ctrl-5 (German keyboard))
# xm console [guest_name]
Shutdown a guest
# xm shutdown [guest_name]
Destroy (Power off) a guest
# xm destroy [guest_name]
Monitor guests
# xm top
virsh commands
# virsh
virsh # help
virsh start [guest_name]
OpenWrt
OpenWrt is described as a Linux distribution for embedded devices.
Instead of trying to create a single, static firmware, OpenWrt provides a fully writable filesystem with package management. This frees you from the application selection and configuration provided by the vendor and allows you to customize the device through the use of packages to suit any application. For developer, OpenWrt is the framework to build an application without having to build a complete firmware around it; for users this means the ability for full customization, to use the device in ways never envisioned.
via OpenWrt.
Welcome to the Tomato USB web site
Tomato USB is an alternative Linux-based firmware for powering Broadcom-based ethernet routers. It is a modification of the famous Tomato firmware, with additional built-in support for USB port, wireless-N mode support, support for several newer router models, and various enhancements.
Steve Jobs Solved the Innovator’s Dilemma
By taking this approach, Apple bent all the rules of disruption. To disrupt yourself, for example, Professor Christensen’s research would typically prescribe setting up a separate company that eventually goes on to defeat the parent. It’s incredibly hard to do this successfully; Dayton Dry Goods pulled it off with Target. IBM managed to do it with the transition from mainframes to PCs, by firewalling the businesses in entirely different geographies. Either way, the number of companies that have successfully managed to do it is a very, very short list. And yet Apple’s doing it to itself right now with the utmost of ease. Here’s new CEO Tim Cook, on the iPad disrupting the Mac business: “Yes, I think there is some cannibalization… the iPad team works on making their product the best. Same with the Mac team.” It’s almost unheard of to be able to manage disruption like this.
via Steve Jobs Solved the Innovator’s Dilemma – James Allworth – Harvard Business Review.
Wi-Fi devices crowd 2.4GHz band; IT looks to 5GHz
Kobo Vox Tech Specs
Kobo Vox
An eReader and so much more!
- Revolutionary new social reading experience
- Built-in Wi Fi for life on the go
- Web, email, music, video and over
500,000 apps for Android on Google PlayTM!
Enterprise Storage Encryption: An Administrator’s …
Storage encryption has historically proven unpopular because of the issues of managing the keys used in various encryption methods, and the system performance burden that encryption/decryption placed on systems hardware. These issues have been iteratively surmounted in a number of advances. Faster CPUs, disk controllers and host bus adapters (HBAs) and tough-to-break encryption now reduce the burden once placed on subsystem, disk, and device encryption.
via Enterprise Storage Encryption: An Administrator’s … – Input Output.
This is a pretty good article. Here’s one more blurb.
Subsystems are encrypted at the hardware level or at the device group level. Subsystems can also be encrypted by the use of third-party software packages designed specifically for this purpose. Subsystem encryption usually means that a single encryption key is used for the group, and that the private encryption key is stored in hardware or in system firmware. This type of protection means that a drive “stolen” or otherwise removed from the group of storage media can’t be decrypted, even by examining the disk using an identical system, as the identical system would be missing the key that unlocks the data by decrypting it.
This seems like a rather high level of security.
Cherokee web server vs Apache httpd web server
Cherokee web server vs Apache httpd web server | Craig Strong.
Although I was impressed so far, the remaining challenge that Cherokee must live up to for me is it’s speed advantages. In the spirit of keeping things simple and to get a loose overview on performance advantages I thought I’d simply use ‘Zend Controller’ which is bundled with ‘Zend Server CE‘ to test how many requests per second both Apache and Cherokee could handle in turn upon my humble local virtual machine. From these tests I obtained the following results :
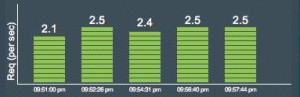
Apache Web Server Results
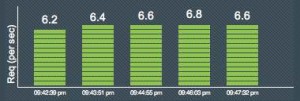
Cherokee Web Server Results
What happens to data when your cloud provider evaporates?
Currently, there’s no way for a cloud storage service provider to directly migrate customer data to another provider. If a service goes down, the hosting company must return the data to its customer, who then must find another provider or revert back to storing it locally, according to Arun Taneja, principal analyst at The Taneja Group.
via What happens to data when your cloud provider evaporates? – Computerworld.
This is only a problem if you don’t have a physical backup of your own data somewhere under your control. Expecting the cloud to be the end all be all for all IT needs is a mistake IMHO. Don’t put all your eggs in one basket. The cloud does serve useful purposes.
Ask Ars: what’s the relationship between CPU clockspeed and performance?
Question: Intel’s Sandy Bridge launch just brought its desktop CPU line up to 3.8GHz, but I remember that the Pentium 4 got up to 3.8GHz before being cancelled. So why is it that Sandy Bridge is just now getting to the clock speed levels that the Pentium 4 was at years ago? And how is it that Sandy Bridge still manages to outperform the older Pentium 4, even though it has a lower clock speed?
via Ask Ars: what’s the relationship between CPU clockspeed and performance?.
Worth a read.