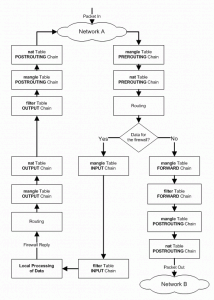
nftables is the project that aims to replace the existing {ip,ip6,arp,eb}tables framework. Basically, this project provides a new packet filtering framework, a new userspace utility and also a compatibility layer for {ip,ip6}tables. nftables is built upon the building blocks of the Netfilter infrastructure such as the existing hooks, the connection tracking system, the userspace queueing component and the logging subsystem.
via netfilter/iptables project homepage – The netfilter.org “nftables” project.
From: Nftables: a new packet filtering engine
Packet filtering and firewalling has a long history in Linux. The first filtering mechanism, called “ipfwadm,” was released in 1995 for the 1.2.1 kernel. This code was used until the 2.2.0 stable release (January, 1999), when the new “ipchains” module took over. While ipchains was useful, it only lasted until 2.4.0 (January, 2001), when it, too, was replaced by iptables/netfilter, which remains in the kernel now. If netfilter maintainer Patrick McHardy has his way, though, iptables, too, will be gone in the future, replaced by yet another mechanism called “nftables.” This article will give an overview of how nftables works, followed by a discussion of the motivations behind this change.