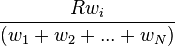Whereas the telcos are migrating from voice-centric architectures to flat, all-IP networks, cable operators are set to go through a similar transition, but from video-centric to IP-centric networks.
Tag Archives: protocols
Juniper Targets SDN With Another Core Switch
The new direction that the switch represents is programmability. As SDN develops, more and more protocols are coming into play. VXLAN from VMware Inc. and NVGRE from Microsoft Corp. would be two examples, both being protocols for moving virtual machines around the network.
via Light Reading – Juniper Targets SDN With Another Core Switch.
MultiPath TCP
MultiPath TCP (MPTCP) is an effort towards enabling the simultaneous use of several IP-addresses/interfaces by a modification of TCP that presents a regular TCP interface to applications, while in fact spreading data across several subflows. Benefits of this include better resource utilization, better throughput and smoother reaction to failures. Slides – explaining MultiPath TCP – are available in .pdf and .pptx format. You can also have a look at our Google Techtalk about MPTCP.
via MultiPath TCP – Linux Kernel implementation : Main – Home Page browse.
50 Million Potentially Vulnerable to UPnP Flaws
Between June 1 and Nov. 17, 2012, Rapid7 conducted weekly scans that sent simple service discovery protocUPnPol SSDP requests to each routable IPv4 address. In all, 2.2 percent of all public IPv4 addresses responded to the standard UPnP discovery requests. So, 81 million unique IP addresses responded and, upon deeper probing, researchers determined some 17 million further systems exposed the UPnP simple object access protocol SOAP. This level of exposure was far higher than researchers had expected, according to the report.
via 50 Million Potentially Vulnerable to UPnP Flaws | threatpost.
BitTorrent Launches Private and Secure Dropbox Alternative
Just ask Twitter and Facebook, two major technology companies that rely on BitTorrent technology to distribute files across their networks.
via BitTorrent Launches Private and Secure Dropbox Alternative | TorrentFreak.
I didn’t know that about facebook and twitter. Bittorrent is a very useful protocol for certain use cases and I’m surprised other cloud storage providers haven’t adopted it yet.
Errata Security: Apple’s secret “wispr” request
The reason Apple does this is because you may be using an app other than the web browser. For example, the only thing you might be doing is syncing your e-mail. In such situations, you would never see the portal page, and your app will mysteriously fail to connect to the Internet.
Therefore, before your app has a chance to access the network, Apple does this for you. It sends out a request to the above URL. If the request gets redirected, then Apple knows there is a portal. It then launches a dialog box, containing Safari, to give you a chance to login.
via Errata Security: Apple’s secret “wispr” request.
At my local Starbucks, all web surfing is free. But, Windows presents a captive logon page where you must accept the Terms of Service, but the iPhone doesn’t. I assume the portal detects this URL, and automatically opens up the access-point without doing a redirection. I need to test witha Linux distro in order to figure out what’s going on.
Cisco Takes Location Indoors
Cisco is using its Mobility Services Advertisement Protocol (MSAP) client as the frontend to triangulate location data from small cells and Wi-Fi so that it can map out the locations of stores and more on different floors inside a building. Qualcomm will build this capability into the next generation of its Snapdragon chips for mobile devices, but Cisco is offering the software to enterprises now.
via Cisco Takes Location Indoors – IP & Convergence – Telecom News Analysis – Light Reading Mobile.
New WiFi protocol boosts congested wireless network throughput by 700%
To solve this problem, NC State University has devised a scheme called WiFox. In essence, WiFox is some software that runs on a WiFi access point (i.e. it’s part of the firmware) and keeps track of the congestion level. If WiFox detects a backlog of data due to congestion, it kicks in and enables high-priority mode. In this mode, the access point gains complete control of the wireless network channel, allowing it to clear its backlog of data. Then, with the backlog clear, the network returns to normal.
via New WiFi protocol boosts congested wireless network throughput by 700% | ExtremeTech.
Vint Cerf and NASA’s BP and DTN Protocol: How It Works
The big difference between BP and IP is that, while IP assumes a more or less smooth pathway for packets going from start to end point, BP allows for disconnections, glitches and other problems you see commonly in deep space, Younes said. Basically, a BP network — the one that will the Interplanetary Internet possible — moves data packets in bursts from node to node, so that it can check when the next node is available or up.
via Vint Cerf and NASA’s BP and DTN Protocol: How It Works.
DTN = Disruption Tolerant Networking
Ericsson Adapts to the TV Streaming Challenge
The problem with ABR is that the client device, such as a smartphone or tablet, is in charge of the bandwidth and isn’t fair about how that capacity is allocated. If an iPhone is the first device on the home network to request a video stream, it will typically receive a high bit-rate version — perhaps more than it really needs. Then, when a connected HD television requests a stream, it tends to get the scraps, resulting in a crummy-looking pixel-icious image.
Ericsson AB (Nasdaq: ERIC) is trying to solve the problem by applying Weighted Fair Queuing (WFQ), a data packet scheduling technique, to ABR streams.
From Wikipedia on WFQ:
WFQ is a generalization of fair queuing (FQ). Both in WFQ and FQ, each data flow has a separate FIFO queue. In FQ, with a link data rate of
, at any given time the
active data flows (the ones with non-empty queues) are serviced simultaneously, each at an average data rate of
. Since each data flow has its own queue, an ill-behaved flow (who has sent larger packets or more packets per second than the others since it became active) will only punish itself and not other sessions.
As opposed to FQ, WFQ allows different sessions to have different service shares. If
data flows currently are active, with weights
data flow number
will achieve an average data rate of
It can be proven [1] that when using a network with WFQ switches and a data flow that is leaky bucket constrained, an end-to-end delay bound can be guaranteed. By regulating the WFQ weights dynamically, WFQ can be utilized for controlling the quality of service, for example to achieve guaranteed data rate.