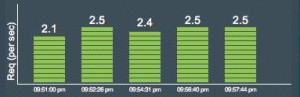
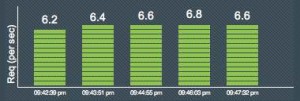
With so many use cases and potential buyers, the vendors too often try to be everything to everyone. The result is a class of products that suffers from an identity crisis — so-called business storage solutions that are overloaded with consumer features and missing the ease and simplicity that business users require.
via NAS shoot-out: 5 storage servers battle for business | Storage – InfoWorld.
I found the below snippet to be interesting.
Connecting the NAS boxes to your network should be done via a wired Ethernet cable, and each NAS in this roundup should get two Gigabit Ethernet connections. Strictly speaking, you need only one of these links, but by using both, you gain much greater flexibility. You should use them in a fail-over configuration, which means that if one of your Ethernet cables loses signal, the other will take over. You should also “bond” the two connections together to increase throughput or to balance the network load.
Also.
NAS shoot-out: Everything else but the kitchen sink
All of the NAS boxes in this roundup have the flexibility to do more than merely store your data. These features are too numerous to review in detail, but they include such things as the ability to collect images from IP video surveillance cameras, mobile apps that allow you to access your data from iPhones, iPads, and Android devices, and multimedia servers that provide access to photos, music, and video.
In addition to the built-in features, you can generally install software packages that extend the functionality. Typical add-on modules include BitTorrent downloaders, email servers, and content management and blog publishing applications.